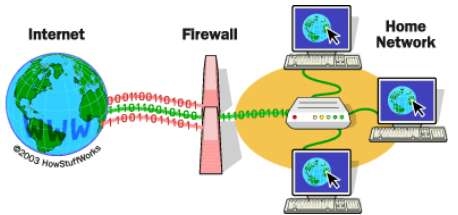
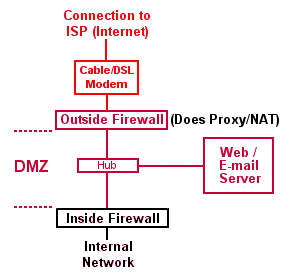
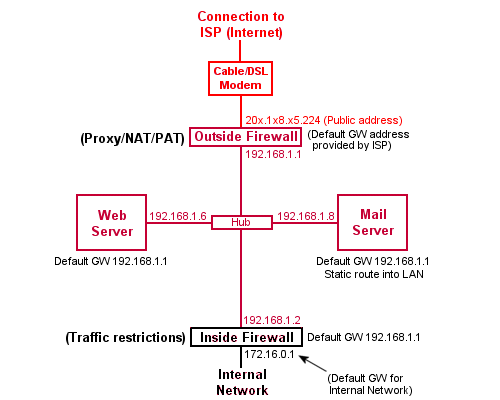
Proxy, NAT, Firewall Aquest apartat és una ampliació de l'apartat Proxy Server, que prenem com a punt de partida. Es convenient familiaritzar-se una mica més amb el comandament iptables. Aquí trobareu una mica més d'informació. El que farem ara és ampliar el script que ja havíem fet servir, ampliant el seu ús a tres tipus de regles: input, output and forwarding: INPUT: Trafic destinat al servidor mateix. FORWARD: Tràfic amb origen remot i destinació remota. OUTPUT: Tràfic generat al servidor amb destinació local o remota. Utilitzarem el següent script: #!/bin/sh # IPTABLES FIREWALL script for the Linux 2.4 kernel. # This script is a derivitive of the script presented in # the IP Masquerade HOWTO page at: # www.tldp.org/HOWTO/IP-Masquerade-HOWTO/stronger-firewall-examples.html # It was simplified to coincide with the configuration of # the sample system presented in the Guides section of # www.aboutdebian.com # # This script is presented as an example for testing ONLY # and should not be used on a production firewall server. # # PLEASE SET THE USER VARIABLES # IN SECTIONS A AND B OR C echo -e "\n\nSETTING UP IPTABLES FIREWALL..." # === SECTION A # ----------- FOR EVERYONE # SET THE INTERFACE DESIGNATION AND ADDRESS AND NETWORK ADDRESS # FOR THE NIC CONNECTED TO YOUR _INTERNAL_ NETWORK # The default value below is for "eth0". This value # could also be "eth1" if you have TWO NICs in your system. # You can use the ifconfig command to list the interfaces # on your system. The internal interface will likely have # have an address that is in one of the private IP address # ranges. # Note that this is an interface DESIGNATION - not # the IP address of the interface. # Enter the designation for the Internal Interface's INTIF="eth1" # Enter the NETWORK address the Internal Interface is on INTNET="192.168.2.0/24" # Enter the IP address of the Internal Interface INTIP="192.168.2.1/24" # SET THE INTERFACE DESIGNATION FOR YOUR "EXTERNAL" (INTERNET) CONNECTION # The default value below is "ppp0" which is appropriate # for a MODEM connection. # If you have two NICs in your system change this value # to "eth0" or "eth1" (whichever is opposite of the value # set for INTIF above). This would be the NIC connected # to your cable or DSL modem (WITHOUT a cable/DSL router). # Note that this is an interface DESIGNATION - not # the IP address of the interface. # Enter the external interface's designation for the # EXTIF variable: EXTIF="eth0" # ! ! ! ! ! Use ONLY Section B *OR* Section C depending on # ! ! ! ! the type of Internet connection you have. # ! ! ! ! ! Uncomment ONLY ONE of the EXTIP statements. # === SECTION B # ----------- FOR THOSE WITH STATIC PUBLIC IP ADDRESSES # SET YOUR EXTERNAL IP ADDRESS # If you specified a NIC (i.e. "eth0" or "eth1" for # the external interface (EXTIF) variable above, # AND if that external NIC is configured with a # static, public IP address (assigned by your ISP), # UNCOMMENT the following EXTIP line and enter the # IP address for the EXTIP variable: EXTIP="192.168.1.19" # === SECTION C # ---------- DIAL-UP MODEM, AND RESIDENTIAL CABLE-MODEM/DSL (Dynamic IP) USERS # SET YOUR EXTERNAL INTERFACE FOR DYNAMIC IP ADDRESSING # If you get your IP address dynamically from SLIP, PPP, # BOOTP, or DHCP, UNCOMMENT the command below. # (No values have to be entered.) # Note that if you are uncommenting these lines then # the EXTIP line in Section B must be commented out. #EXTIP="`/sbin/ifconfig ppp0 | grep 'inet addr' | awk '{print $2}' | sed -e 's/.*://'`" # -------- No more variable setting beyond this point -------- echo "Loading required stateful/NAT kernel modules..." /sbin/depmod -a /sbin/modprobe ip_tables /sbin/modprobe ip_conntrack /sbin/modprobe ip_conntrack_ftp /sbin/modprobe ip_conntrack_irc /sbin/modprobe iptable_nat /sbin/modprobe ip_nat_ftp /sbin/modprobe ip_nat_irc echo " Enabling IP forwarding..." echo "1" > /proc/sys/net/ipv4/ip_forward echo "1" > /proc/sys/net/ipv4/ip_dynaddr echo " External interface: $EXTIF" echo " External interface IP address is: $EXTIP" echo " Loading firewall server rules..." UNIVERSE="0.0.0.0/0" # Clear any existing rules and setting default policy to DROP iptables -P INPUT DROP iptables -F INPUT iptables -P OUTPUT DROP iptables -F OUTPUT iptables -P FORWARD DROP iptables -F FORWARD iptables -F -t nat # Flush the user chain.. if it exists if [ "`iptables -L | grep drop-and-log-it`" ]; then iptables -F drop-and-log-it fi # Delete all User-specified chains iptables -X # Reset all IPTABLES counters iptables -Z # Creating a DROP chain iptables -N drop-and-log-it iptables -A drop-and-log-it -j LOG --log-level info iptables -A drop-and-log-it -j REJECT echo -e " - Loading INPUT rulesets" ####################################################################### # INPUT: Incoming traffic from various interfaces. All rulesets are # already flushed and set to a default policy of DROP. # # loopback interfaces are valid. iptables -A INPUT -i lo -s $UNIVERSE -d $UNIVERSE -j ACCEPT # local interface, local machines, going anywhere is valid iptables -A INPUT -i $INTIF -s $INTNET -d $UNIVERSE -j ACCEPT # remote interface, claiming to be local machines, IP spoofing, get lost iptables -A INPUT -i $EXTIF -s $INTNET -d $UNIVERSE -j drop-and-log-it # remote interface, any source, going to permanent PPP address is valid iptables -A INPUT -i $EXTIF -s $UNIVERSE -d $EXTIP -j ACCEPT # Allow any related traffic coming back to the MASQ server in iptables -A INPUT -i $EXTIF -s $UNIVERSE -d $EXTIP -m state --state ESTABLISHED,RELATED -j ACCEPT # OPTIONAL: Uncomment the following two commands if plan on running # an Apache Web site on the firewall server itself # #echo -e " - Allowing EXTERNAL access to the WWW server" #iptables -A INPUT -i $EXTIF -m state --state NEW,ESTABLISHED,RELATED -p tcp -s $UNIVERSE -d $EXTIP --dport 80 -j ACCEPT # Catch all rule, all other incoming is denied and logged. iptables -A INPUT -s $UNIVERSE -d $UNIVERSE -j drop-and-log-it echo -e " - Loading OUTPUT rulesets" ####################################################################### # OUTPUT: Outgoing traffic from various interfaces. All rulesets are # already flushed and set to a default policy of DROP. # # loopback interface is valid. iptables -A OUTPUT -o lo -s $UNIVERSE -d $UNIVERSE -j ACCEPT # local interfaces, any source going to local net is valid iptables -A OUTPUT -o $INTIF -s $EXTIP -d $INTNET -j ACCEPT # local interface, any source going to local net is valid iptables -A OUTPUT -o $INTIF -s $INTIP -d $INTNET -j ACCEPT # outgoing to local net on remote interface, stuffed routing, deny iptables -A OUTPUT -o $EXTIF -s $UNIVERSE -d $INTNET -j drop-and-log-it # anything else outgoing on remote interface is valid iptables -A OUTPUT -o $EXTIF -s $EXTIP -d $UNIVERSE -j ACCEPT # Catch all rule, all other outgoing is denied and logged. iptables -A OUTPUT -s $UNIVERSE -d $UNIVERSE -j drop-and-log-it echo -e " - Loading FORWARD rulesets" ####################################################################### # FORWARD: Enable Forwarding and thus IPMASQ # Allow all connections OUT and only existing/related IN iptables -A FORWARD -i $EXTIF -o $INTIF -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A FORWARD -i $INTIF -o $EXTIF -j ACCEPT # Catch all rule, all other forwarding is denied and logged. iptables -A FORWARD -j drop-and-log-it # Enable SNAT (MASQUERADE) functionality on $EXTIF iptables -t nat -A POSTROUTING -o $EXTIF -j SNAT --to $EXTIP echo -e " Firewall server rule loading complete\n\n" Anem a descriure els paràmetres introduïts al script: Secció A Internal interface designation (INTIF); INTIF="eth1" Internal network address (INTNET); INTNET="192.168.2.0/24" Internal interface IP address (INTIP); INTIP="192.168.2.1/24" External interface designation (EXTIF); EXTIF="eth0" Secció B Static IP address of external interface (EXTIP); EXTIP="192.168.1.19" Fixem-nos en l'acció 'drop-and-log-it' a les regles 'catch all'. Els missatges generats pel comandament IPTABLES es poden veure al fitxer /var/log/messages i també a la consola. Aquests missatges inclouen les adreces IP de la font i la destinació dels paquets descartats. La línia UNIVERSE="0.0.0.0/0" significa "qualsevol adreça". Una bona disposició dels elements d'un sistema que es pot protegir de manera òptima és la que es veu a les figures: Establirem una part de la xarxa com a DMZ, (demilitarized zone). Això voldrà dir que el tallafocs interior haurà de permetre l'accés exterior de determinats ordinadors. A més hem de permetre un accés restringit a determinats ports que haurà de ser dirigit de manera preestablerta a determinats ordinadors. Aquesta última funció reb el nom de PAT, (Port Address Translation). Expliquem aquestes qüestions al següent apartat. DMZ i PAT Ara definim un nou paràmetre, la IP del servidor, i ho afegim a la secció de definició de variables a l'inici del script # === EXTRA PER A DMZ / PAT # IP estàtica del servidor SERVERIP = "192.168.2.12" i després substituïm l'ultim apartat del final del script per a poder redireccionar els paquets al port 80 al nostre servidor: ####################################################################### # FORWARD: Enable Forwarding and thus IPMASQ # Allow all connections OUT and only existing/related IN iptables -A FORWARD -i $EXTIF -o $INTIF -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A FORWARD -i $INTIF -o $EXTIF -j ACCEPT # Allow forwarding of incoming Port 80 traffic to DMZ Web server iptables -A FORWARD -i $EXTIF -o $INTIF -d $SERVERIP -p tcp --dport 80 -j ACCEPT # Catch all rule, all other forwarding is denied and logged. iptables -A FORWARD -j drop-and-log-it # Enable SNAT (MASQUERADE) functionality on $EXTIF iptables -t nat -A POSTROUTING -o $EXTIF -j SNAT --to $EXTIP # Enable DNAT port translation to DMZ Web server iptables -t nat -A PREROUTING -i $EXTIF -d $EXTIP -p tcp --dport 80 -j DNAT --to $SERVERIP echo -e " Firewall server rule loading complete\n\n" Després en un terminal posem les coses a lloc chmod 755 /etc/init.d/firewall.sh i executem el script: sudo /etc/init.d/firewall.sh I funciona!!! (*) The ESTABLISHED keyword in the rule that fowards packets from the External (Internet) interface to the Internal (LAN) interface limits incoming traffic to that which is a "response" to a previously sent outgoing request (a Web page coming back from a browser request for example). Si necessiteu resoldre algun dubte, poseu-vos en contacte a través d'aquest enllaç. |
10. Firewall |